Exploring Active and Passive Learning in Cybersecurity
Written on
Introduction to Cognitive Psychology in Cybersecurity
Cognitive psychology examines how humans process various forms of information, including attention, memory, problem-solving, and reasoning. This field extends beyond mere learning, influencing all facets of cybersecurity, from behavior and biometrics to social engineering. Essentially, it seeks to understand human behavior, which bears resemblance to the foundations of Artificial Intelligence (AI).
In this discussion and future explorations, we will leverage insights from cognitive psychologists and neuroscientists to enhance our understanding of cybersecurity. Furthermore, I will revisit previous articles to integrate these valuable concepts. As a cybersecurity expert with 17 years of experience and a keen interest in cognitive psychology, I've applied these methodologies and observed marked improvements in my knowledge retention and problem-solving abilities.
Passive Learning in Cybersecurity
Passive learning is precisely what it implies: a lack of active engagement in the learning process. Typically, we merely repeat information received from textbooks or instructors. Knowledge tends to pass through us with little retention, often resulting in a mere 10% comprehension of the material covered.
Examples of passive learning include:
- Highlighting texts
- Observing examples
- Transcribing lecture slides
- Noting what is said in class
- Reviewing notes prior to exams
- Memorization techniques
- Following walkthroughs in homelab capture the flags
Active Learning in Cybersecurity
In contrast, active learning engages our cognitive faculties to forge connections between concepts. This approach necessitates mental engagement with the subject matter before recording information, practicing topics without notes, and developing questions prior to lectures or readings. While active learning may demand more time than passive methods, it ultimately leads to greater retention and understanding.
Examples of active learning practices include:
- Creating detailed mind maps
- Solving example problems independently
- Formulating insightful questions for post-lecture discussion
- Summarizing key points after lectures or readings
- Teaching the material to others
- Engaging in personal labs and capture the flags without assistance
- Delaying note-taking until after reading
Combining Learning Techniques
In the realm of cybersecurity, not every concept requires deep analysis. For instance, when deciding between analyzing protocols and memorizing port numbers, one must engage in active thought.
If you concluded that protocols warrant analysis while port numbers can be memorized, you're spot on! To illustrate, consider creating a mind map comparing TCP and UDP:
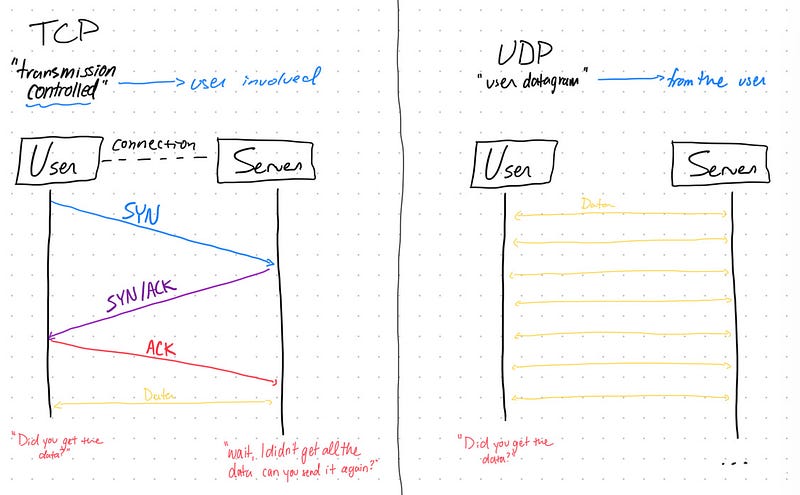
For port numbers, simple memorization suffices since they are arbitrary numbers assigned by IANA.
While both learning styles are essential, initiating with active learning allows us to grasp concepts intuitively. Attempting to memorize port numbers before understanding protocols can hinder natural cognitive processes. Thus, starting with protocols followed by port numbers proves to be more effective.
Overview of Learning in Cybersecurity
Learning should pose challenges. Passive learning does not stimulate our cognitive capabilities, rendering the experience tedious and inefficient. Conversely, active learning leverages our cognitive abilities to create connections, apply knowledge, and fosters higher retention rates.
A special acknowledgment goes to Justin Sung on YouTube, whose content has been invaluable in my learning journey!
Helpful Resources:
Explore the distinctions between active and passive reconnaissance in cybersecurity.
An overview of passive versus active tools and techniques for beginners in cybersecurity training.