Understanding Threat Modeling: A Comprehensive Overview
Written on
Chapter 1: Introduction to Threat Modeling
Threat modeling is a systematic approach to recognizing and ranking potential threats and vulnerabilities. This process also involves prioritizing strategies to safeguard assets, including sensitive information and intellectual property.
Threat modeling is essential in identifying and addressing security concerns effectively.
Section 1.1: Key Principles of Threat Modeling
To effectively implement threat modeling, it’s vital to establish the scope and depth of the analysis. Begin by understanding the components involved—creating a diagram or flowchart of how various systems are interconnected is beneficial.
Next, model potential attack scenarios by identifying assets, security controls, and threat agents to form a security framework. This stage involves pinpointing specific threats and assessing any gaps in security measures.
Subsection 1.1.1: STRIDE Methodology
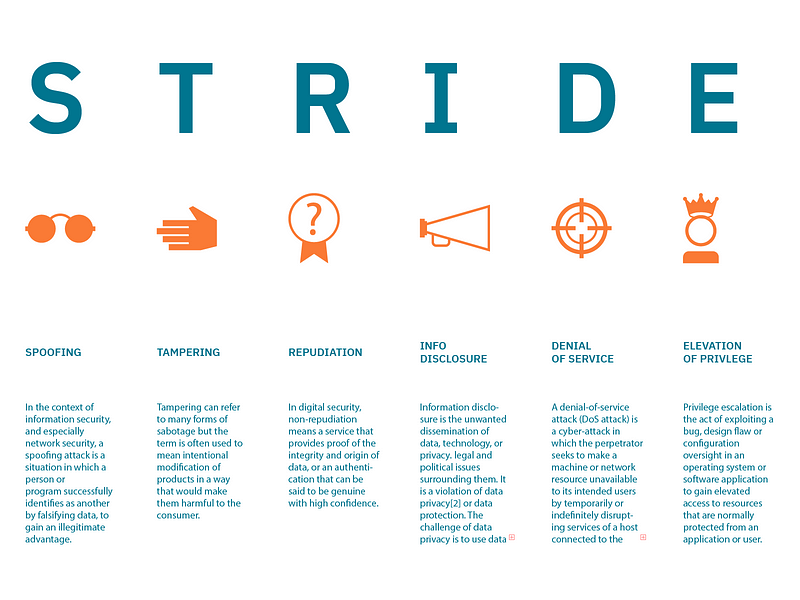
STRIDE is an acronym for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service (DoS), and Elevation of Privilege. Developed by Microsoft, this framework assists applications in adhering to security standards based on the core principles of confidentiality, integrity, and availability. STRIDE categorizes security threats into six distinct categories.
Chapter 1.2: Additional Methodologies
Threat modeling can also be approached through various methodologies, each with unique perspectives.
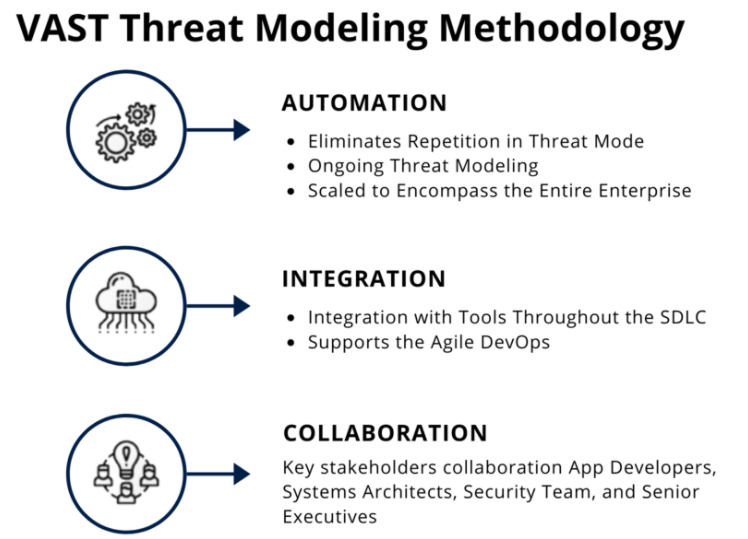
The Visual, Agile, and Simple Threat (VAST) Model, for instance, emphasizes a comprehensive view throughout the software development lifecycle (SDLC) within an organization.
The Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) process focuses primarily on strategic risk assessment. It emphasizes understanding organizational risks with minimal emphasis on technological vulnerabilities. This model comprises three phases: building asset-based threat profiles, identifying infrastructure vulnerabilities, and developing a security strategy.

Chapter 2: Advanced Threat Modeling Approaches
The Process for Attack Simulation and Threat Analysis (PASTA) is a risk-centric framework that aligns business objectives with technical requirements, providing an attacker-centric viewpoint to generate asset-focused outcomes.

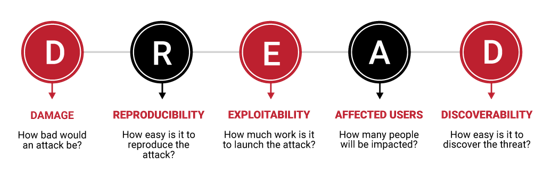
Another notable methodology is the DREAD model, proposed by Microsoft in 2008, which is widely utilized to evaluate security risks based on five categories.
Trike serves as a security audit framework that uses threat models as tools for risk management. It defines acceptable risk levels for each asset and assigns suitable security measures based on the evaluated risks.
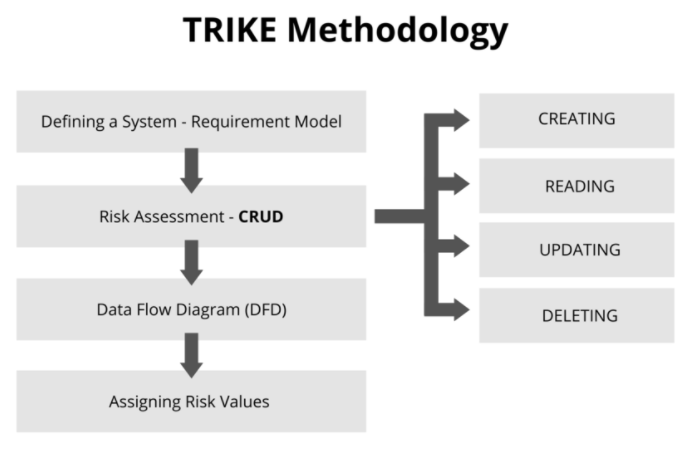
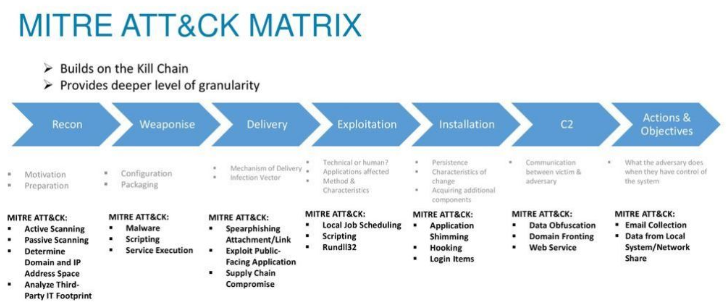
Finally, the MITRE ATT&CK framework offers a globally accessible knowledge base of adversary tactics and techniques, essential for developing effective threat models.
This video titled "STRIDE Threat Modeling for Beginners - In 20 Minutes" provides an accessible introduction to the STRIDE methodology and its application in cybersecurity.
The video "Welcome to the World's Shortest Threat Modeling Course" offers a concise overview of threat modeling concepts, perfect for quick learning.
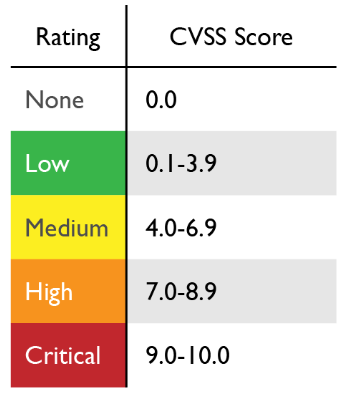
The Common Vulnerability Scoring System (CVSS) method, developed by NIST, evaluates vulnerabilities and assigns severity scores, aiding organizations in prioritizing their security measures effectively.