# Harnessing Google Dorks for Open Source Intelligence
Written on
Chapter 1: Understanding Google Dorks
Google Dorks, often referred to as Google Hacking, is an invaluable technique that should be part of every penetration tester's toolkit. Mastering this skill can significantly enhance your online search capabilities and improve various aspects of your life. When using Google, searches are frequently cluttered with advertisements and sponsored links, so refining your search techniques is essential.
During the initial reconnaissance phase, whether you are conducting a red team exercise or gathering information for a specific target, the first step is always discovery. The objective is to amass as much information as possible, whether for a target or for your own understanding.
If you own a business or work in a small company with limited security resources, performing a Google Dork exercise can reveal insights into what potential attackers might discover about you. Additionally, this exercise can help you gauge your personal visibility online. As our internet presence continues to grow, it's becoming increasingly important to understand how easily someone can find information about you. This awareness is particularly useful when applying for jobs, as many employers conduct preliminary searches to verify your identity.
As you read this, consider searching your username, email address, phone number, or name. You may be surprised at the amount of information that surfaces without even using advanced techniques. For instance, a simple search of one of my domains reveals connections across various sites, some of which I do not control.
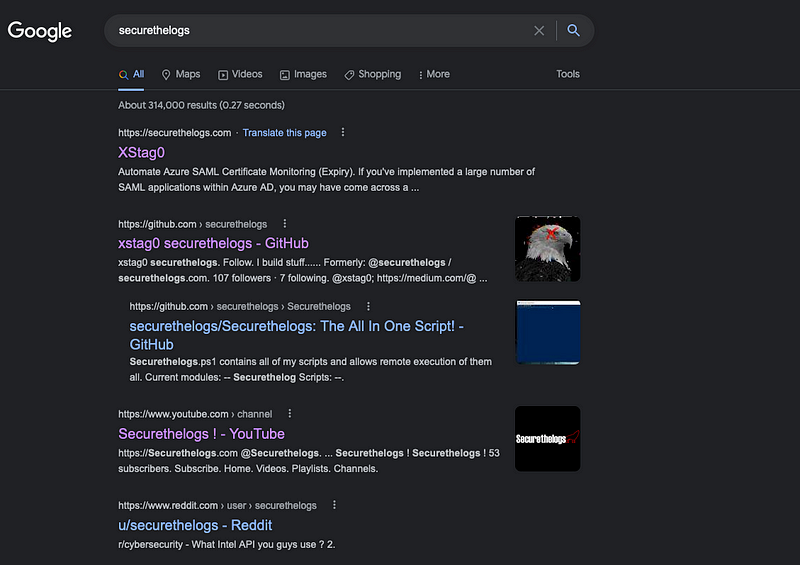
While this isn't an example of dorking, it illustrates how much information Google caches. This vast database of accessible information can be utilized by anyone. It turns out that Google’s capabilities extend far beyond finding dinner recipes.
Another excellent starting point for your search is the advanced search interface. This tool essentially performs the same function as Google Dorking but offers a user-friendly approach. Using the advanced search can make your queries more effective.
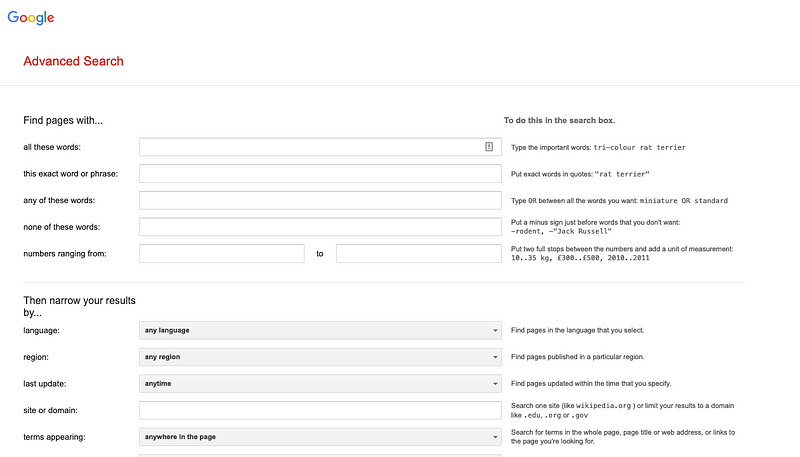
You might be wondering, "Isn't this just regular searching?" You're correct; while it's called Google hacking, it’s really about employing specialized techniques to find exactly what you need—cutting through the noise, so to speak. But why do malicious actors exploit this technique?
In addition to uncovering corporate structures, email addresses, and LinkedIn profiles of executives, they can also identify exposed data or vulnerable systems. For instance, after accessing the Advanced Search feature, you could run a query like allinurl: "admin.php".
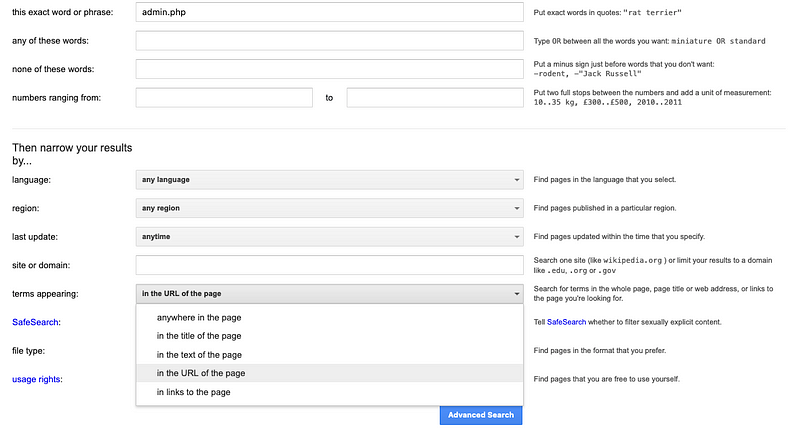
When you execute this query, you may discover links that ideally should not be publicly accessible. While this is a basic search that many are aware of, malicious users would likely search for more specific terms or URL paths within administrative portals.
Now, let’s examine another example. Having previously worked with Symantec, I know the admin login URL. If I were unsure, I could easily find it on the company's website. By utilizing the Advanced Search, I could run a query that leads to multiple companies exposing their Symantec management tools to the internet.
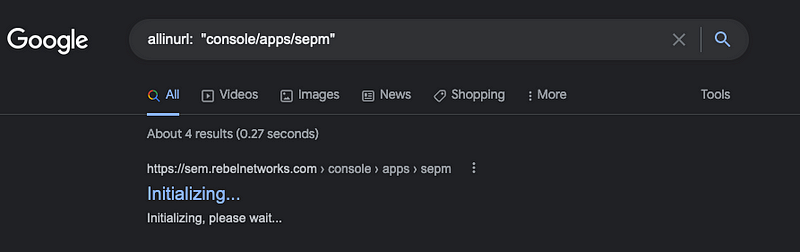
The key here is to think creatively. General searches and social media profiles can provide insight into the technologies a company uses or what an individual relies on, while Google Dorks can help connect the dots.
The potential of Google doesn’t stop with technology. Google provides a wide range of search queries that can be beneficial.
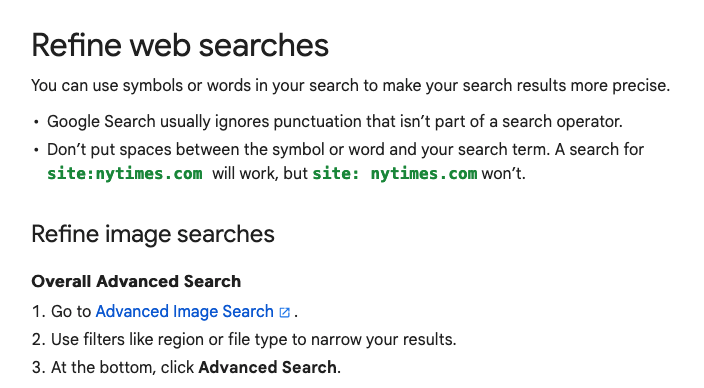
Review the list and start piecing together information. You can search for emails, files, login credentials, usernames, and phone numbers. Begin to consider what you use online and what others might also be using. If you are conducting research, ensure you are familiar with the field or technology in question.
If you’re examining consoles or websites, inspect the site:
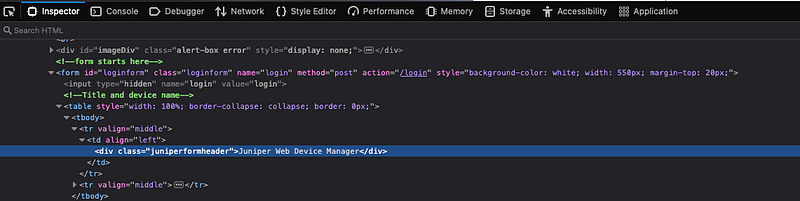
Look for keywords that may not appear in the URL. For example, using intitle: or insite: can help narrow down your searches beyond just URLs.
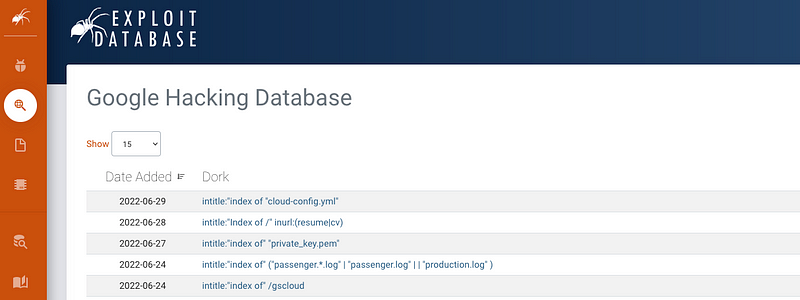
If you're feeling overwhelmed, don’t worry. There is a database that compiles numerous interesting queries you can run. Utilizing these templates will provide greater insight into what queries yield useful results.
Here are a few examples of useful queries:
- Locating indexed SSH private keys: intitle:index.of id_rsa -id_rsa.pub
- Extracting SSH usernames from logs: filetype:log username putty
- Finding open FTP servers: intitle:"index of" inurl:ftp
- Searching for saved email addresses: filetype:xls inurl:"email.xls"
If you wish to target a specific company, you can add a common search term or an additional dork:
"[Keyword]" filetype:xls inurl:"email.xls"
Additionally, for IP-based cameras: inurl:top.htm inurl:currenttime, and for Juniper Web Device Manager Login: intitle:"Log In — Juniper Web Device Manager".
Overall, while Google can be an incredibly useful tool, in the wrong hands, it can also lead to negative outcomes.
If you found this content helpful and want to support, consider subscribing for $5 a month for unlimited access to all stories on Medium. Join today!
Need assistance? Check out my Fiverr or UpWork.
Thank you for taking the time to read!

An overview of OSINT and how Google Dorks can be utilized effectively.
Discover the secrets of OSINT and the power of Google Dorking.